Let’s face it: identity doesn’t show up fully formed. It evolves — often awkwardly — across a series of phases. Most organisations don’t plan these phases out. They happen as a side effect of growth, chaos, mergers, or someone finally yelling, “Wait… who has access to prod?”
Here’s a look at the most common stages organisations go through when it comes to identity — whether they mean to or not.
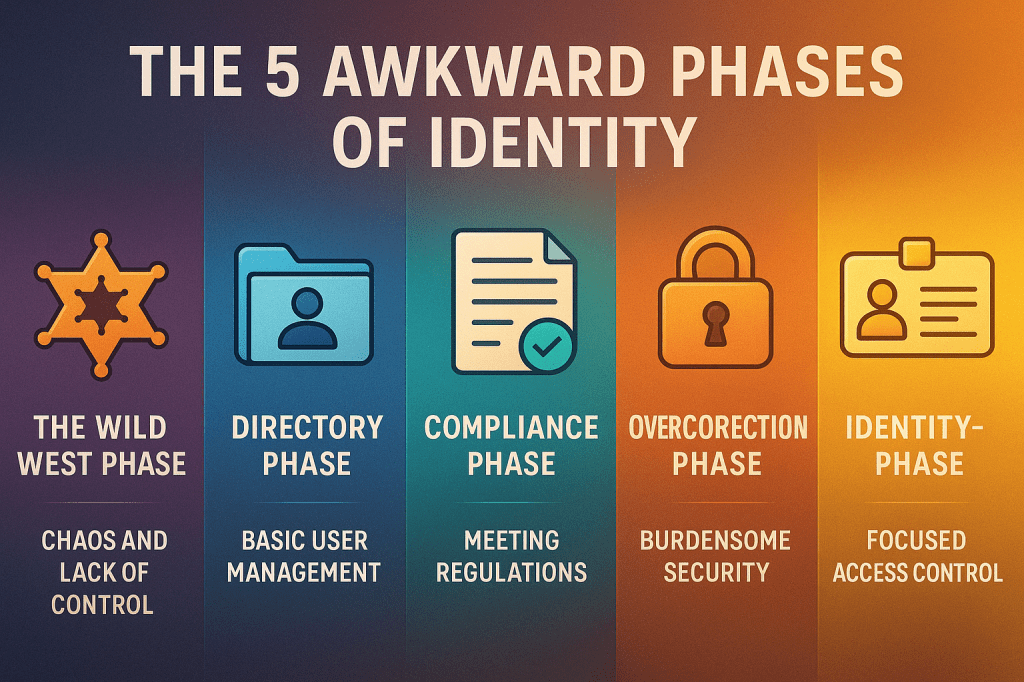
1. The Wild West Phase
Also known as: “Everyone’s an admin and no one audits anything.”
- Shared passwords.
- Local accounts on every server.
- New hire? Copy someone else’s access.
- Offboarding? Eh, probably fine.
This phase often happens early — or after a merger — and usually continues until something breaks… or breaches.
2. The Directory Phase
Also known as: “Let’s centralize. Please. For the love of sanity.”
- A central directory is introduced to bring structure.
- Single Sign-On starts to reduce the tab chaos.
- Access is finally tied to job roles… kind of.
This phase gives some structure, but cracks are already forming. Legacy apps, shadow IT, and cloud services don’t always play nice.
3. The Compliance Phase
Also known as: “We need an audit trail. Yesterday.”
- Certifications, access reviews, MFA requirements.
- Lots of spreadsheets.
- IAM tools start showing up — usually under budget duress.
Security teams start asking hard questions. And the answers aren’t always great. But hey, there’s a process now.
4. The Overcorrection Phase
Also known as: “Now no one can access anything.”
- Overly aggressive policies.
- Too many manual approvals.
- Business users bypass the system because it’s “too locked down.”
This phase tends to cause frustration and sometimes regressions. The challenge: how to balance control with usability.
5. The Identity-First Phase
Also known as: “Let’s design security around identity from day one.”
- Just-in-time access, least privilege, and fine-grained roles.
- Non-human identities treated with the same care as human ones.
- Cloud IAM, PAM, and ISPM tools working together.
This is the phase everyone claims to be in. Very few are. But the ones that are? They sleep a little better at night.
Final Thought
No one gets identity right from day one. It’s a journey — messy, political, sometimes painful. But the organisations that treat identity as a first-class security layer — not just a backend function — are the ones who get ahead of risk.
And more importantly? They get out of the spreadsheet trap.

Leave a comment