Navigating Identity
Behind Every Login, There's a Story
Latest Posts
- The 5 Awkward Phases of Identity (Every Org Goes Through)
- What Employees Actually Expect from Enterprise Identity
- 🔧 Real-World CSMA Patterns (That Actually Show Up in the Wild)
- 🕸️ Cybersecurity Mesh Architecture: A Field Guide for Identity Architects
- 🧟♂️ The IGA Pitfalls That Just Won’t Die(Even After You Threw Budget at Them)
-
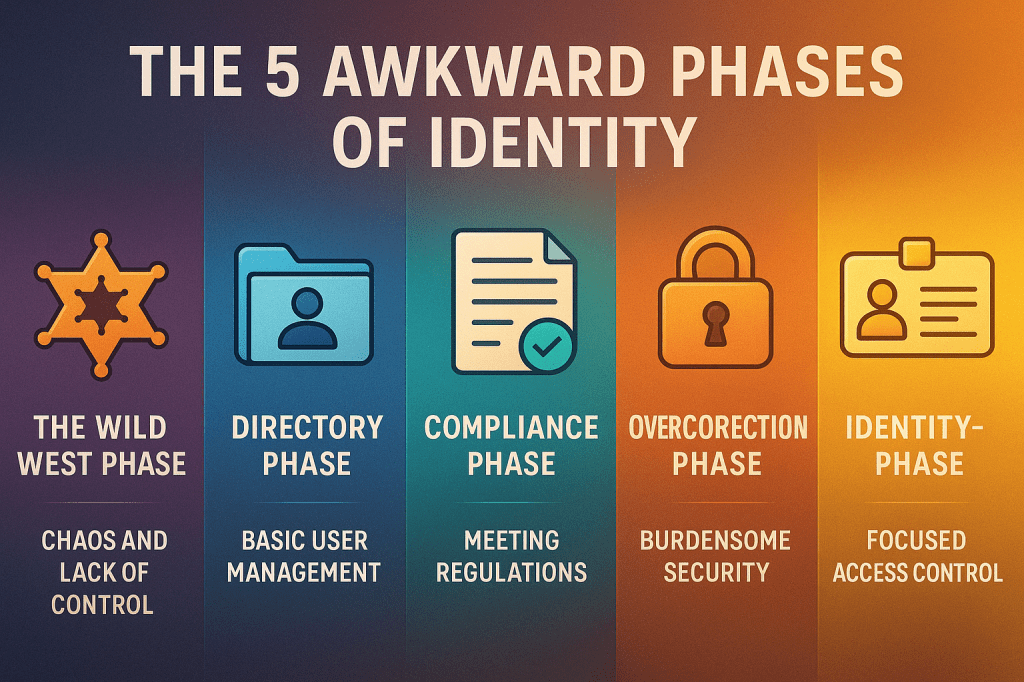
Let’s face it: identity doesn’t show up fully formed. It evolves — often awkwardly — across a series of phases. Most organisations don’t plan these phases out. They happen as a side effect of growth, chaos, mergers, or someone finally yelling, “Wait… who has access to prod?” Here’s a look at the most common stages…
-

Most employees don’t know what “Enterprise Identity” means. They don’t care about acronyms like IAM, IGA, or PAM. What they do care about? Accessing the apps they need. Performing their jobs without unnecessary roadblocks. Avoiding the need to open a help desk ticket just to breathe. So while security teams are busy building out governance…
-

Let’s cut through the theory. Here’s what CSMA looks like when it’s not just a diagram—these are the patterns identity architects are actually stitching into modern environments. 1. API Gateway as a Policy Enforcement Point Instead of leaving access control to backend services, orgs are embedding identity checks at the edge: Why it works: Local…
-

Cybersecurity Mesh Architecture (CSMA) represents a significant transformation in security thinking, emphasizing identity as a central element. It advocates for decentralized, adaptable security measures that assess access based on dynamic context rather than fixed logins. Identity architects must focus on integrating diverse identity systems and creating responsive, continuous trust environments to enhance security management.
-

You got the funding. You picked the platform. You sat through the endless vendor demos and nodded thoughtfully at the implementation roadmap. So why is your identity governance program still… a mess? Because some problems in IGA just don’t stay dead. They keep coming back—quietly, persistently, and usually right before your next audit. Here are…
-

They’re still lurking — despite the roadmap, the audit, and that very convincing slide deck. Let’s be honest: identity security always sounds like a priority… until it’s time to allocate budget, time, or people. Then suddenly, it’s next quarter’s problem. Meanwhile, legacy systems stay exempt from MFA, access reviews get rubber-stamped, and that one service…
-

Role modeling always sounds tidy on a slide deck. But in the real world? It’s a lot like managing your closet. 🧼 Top-Down is the Closet Organizer. You start with a vision. Shirts on hangers, shoes in clear bins, color-coded labels if you’re ambitious. It’s all based on how you think you get dressed —…
-

Customer Identity and Access Management (CIAM) has evolved far beyond login forms and password resets. In 2025, it’s at the heart of how businesses build trust, protect privacy, and deliver seamless digital experiences. Here’s what’s coming next—and what you should be paying attention to. 🔐 1. Passwordless Authentication Grows Up Passwords are on their way…
-

Enterprise Identity in 2025: What Security Leaders Need to Watch In 2025, Enterprise Identity is under more pressure than ever. The traditional boundaries—between user and machine, on-prem and cloud, inside and outside—have collapsed. AI is accelerating both threat and defense. And Identity has become the security control point for everything from Zero Trust to regulatory…